a personal user, to small or large businesses ”
Rapid7
Rapid7 is a unified security operations platform that brings together Vulnerability Management, XDR/SIEM threat detection, and Automated Incident Response into a single, integrated experience. It provides complete visibility into your attack surface and enables faster, more effective mitigation across on-prem, cloud, and hybrid environments.
Designed to reduce SOC workload, improve detection accuracy, accelerate investigation time, and drive measurable security outcomes.
Pentera
Pentera is an automated security validation platform that safely emulates real-world cyberattacks — end-to-end — across networks, identities, endpoints, and cloud assets. Instead of relying solely on scanners or manual penetration testing, Pentera continuously validates how well your existing security controls actually protect your critical assets.
PRE Security
PRE Security is an AI-Native SecOps platform built on the CyberAI architecture that transforms security operations from reactive to predictive and preventive. With Generative XDR™, CyberLLM™, and SOCGPT™, it automates threat detection, response, and forecasting in real-time — empowering SOC teams to stay ahead of attacks before they happen.
Supporting Cloud, Hybrid, and On-Prem environments, PRE Security features Parserless™ data ingestion and seamless integration with existing SIEM or security tools, helping organizations accelerate SecOps modernization without re-engineering legacy systems.
Ping Identity
Ping Identity is an enterprise-grade IAM/CIAM platform that delivers seamless SSO, strong MFA, centralized Access Management, and no-code orchestration with DaVinci. It supports Cloud/Hybrid/On-Prem deployments and open standards—OIDC, SAML, OAuth, FIDO/Passkeys—to secure every user journey while keeping friction low and scale high.
CyCraft
CyCraft is an AI-driven cybersecurity platform that specializes in threat detection and automated incident response. With cutting-edge behavioral analytics and automated investigation, it enables organizations to defend against sophisticated cyber threats in real time.
Orca Security
Orca Security is an agentless-first CNAPP platform that enables organizations to detect cloud vulnerabilities, misconfigurations, exposed data, and identity risks across AWS, Azure, GCP, Kubernetes, and more — all without deploying agents.
Sekoia.io
Sekoia.io is a cloud-native cybersecurity platform that delivers real-time threat detection and response through advanced correlation and automation. It empowers security operations centers (SOCs) to detect threats faster, reduce false positives, and respond more efficiently.
Checkmarx
Checkmarx is a leading application security platform that enables organizations to detect and remediate vulnerabilities across the entire software development lifecycle. Supporting modern DevOps pipelines, it empowers developers and security teams to collaborate more effectively.
Resecurity
Resecurity is a comprehensive cybersecurity platform focused on insider threat protection and cyber threat intelligence. It helps organizations detect data breaches, monitor the dark web, and understand attacker tactics using global threat feeds and proprietary tools.
Proofpoint
Proofpoint is a leading email security solution designed to protect organizations from cyber threats delivered via email. It blocks spam, phishing, malware, and business email compromise (BEC), using advanced threat intelligence and machine learning.



















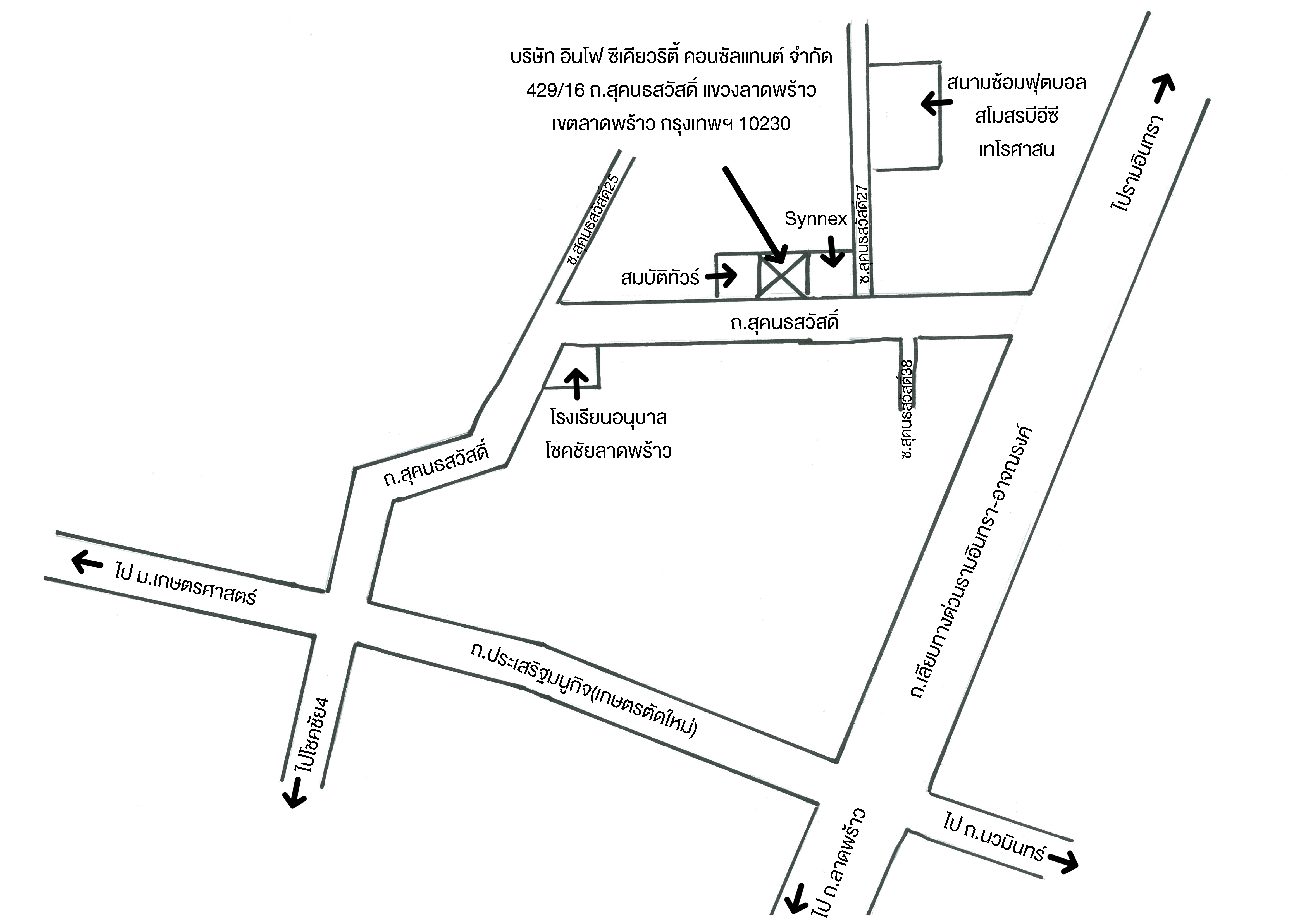
 GOOGLE MAP
GOOGLE MAP INFOSEC MAP
INFOSEC MAP