Key Features:
- Advanced Threat Protection: Detects and blocks malicious attachments, URLs, and zero-day attacks.
- Email Fraud Defense: Identifies email spoofing and impersonation attempts.
- Data Loss Prevention (DLP): Prevents sensitive information from leaking through outbound emails.
- Smart Search Forensics: Provides detailed forensics and threat analysis for administrators to investigate incidents quickly.
- Sandboxing & Dynamic Analysis: Analyzes attachments and links in an isolated environment before delivery.
Key Benefits of Using Proofpoint
1. Comprehensive Protection Against Email Threats
Proofpoint detects and blocks phishing, malware, spam, and zero-day threats before they reach end users—reducing the risk of a successful cyberattack.
2. Business Email Compromise (BEC) and Impersonation Defense
With behavioral analysis and source verification, Proofpoint identifies suspicious sender activity and impersonation attempts that aim to deceive executives or employees.
3. Data Loss Prevention (DLP) with Granular Control
Prevent sensitive data leaks via email with intelligent content scanning and customizable policies to ensure compliance with regulations like GDPR or HIPAA.
4. Accelerated Incident Investigation and Response
The built-in forensics and smart search tools empower security teams to quickly trace, analyze, and remediate email-based attacks—minimizing response time and impact.
5. Improved Cybersecurity Posture and Brand Reputation
By proactively defending against targeted email attacks, organizations enhance their security posture, reduce business risk, and reinforce stakeholder trust.










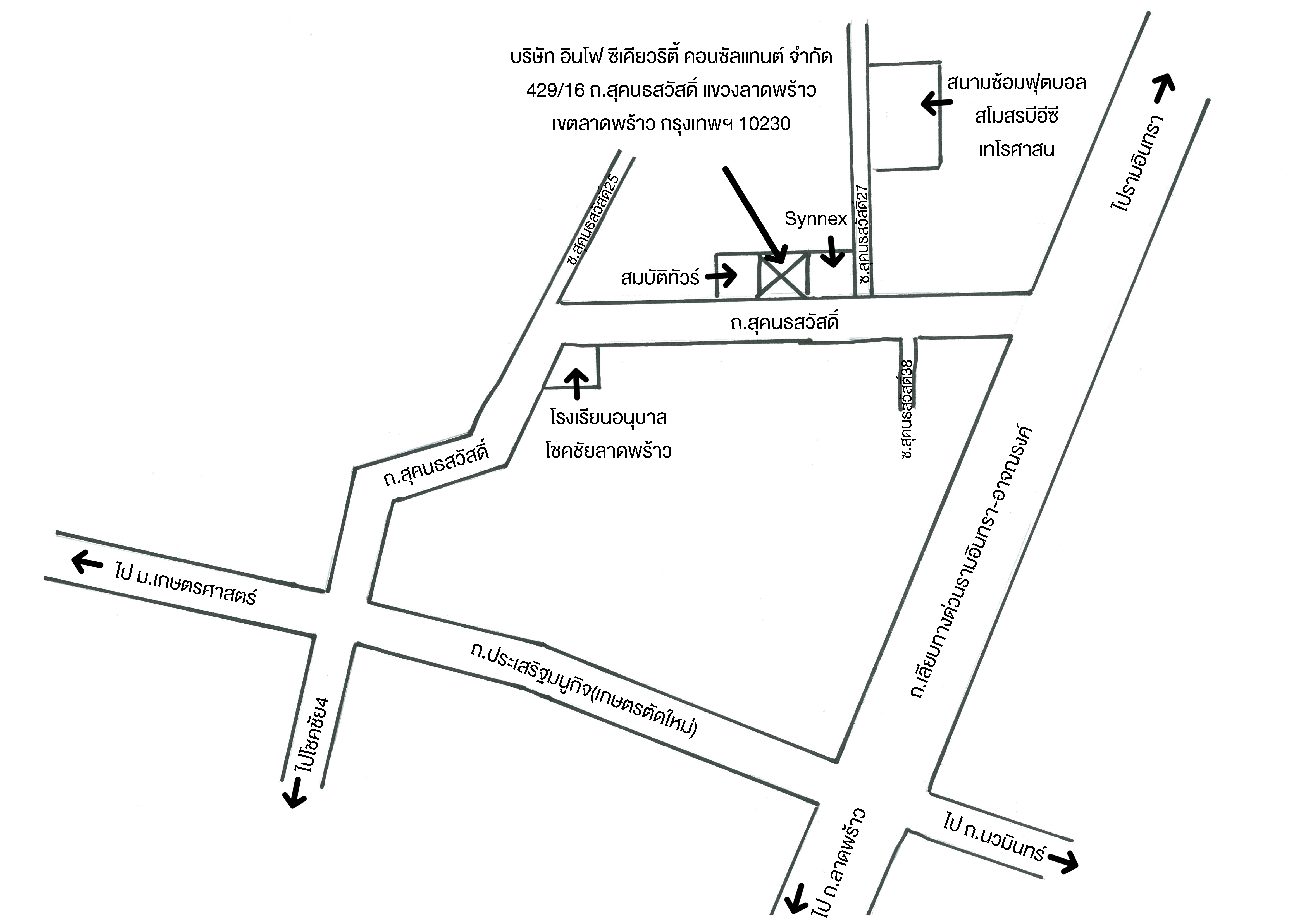
 GOOGLE MAP
GOOGLE MAP INFOSEC MAP
INFOSEC MAP