Cyberattack Alert: Protecting Your Business from Email Spoofing & Phishing Threats
Case Study: Malicious Email Campaign Spoofing Customer Domains to Send Spam and Phishing Links
Event Overview Recently, a malicious email campaign was detected where four domain names were spoofed to send spam and phishing emails to a large number of recipients. The attackers’ intent was to deceive recipients into clicking fake links aimed at stealing personal information, passwords, or financial data.
These emails typically shared the following characteristics:
-
Used legitimate organization domain names in the "From" field to build trust.
-
Attached links to fake websites mimicking the organization's login page.
-
Contained urgent messages such as "Reset Password Immediately," "Check Account Status," or "Pending Documents."
-
Often sent via unauthorized external SMTP relays.
Such incidents pose risks to both the organization's reputation and to end-users who may fall victim to deception.
Comprehensive Cyber Security Solution Protecting Your Organization from Email's Genesis to the Dark Web
-
Email Security & Threat Protection A comprehensive email threat protection system covering every stage of an attack.
Key Features:
-
Phishing & Impersonation Defense
-
Prevents fake emails impersonating executives or business partners by analyzing sender behavior and relationships.
-
-
URL & Attachment Defense
-
All links in emails are rewritten and checked in real-time. If the destination is later changed to a malicious link, the system automatically blocks it.
-
All attachment types are sent to a sandbox for behavioral analysis before reaching the user.
-
-
Auto Pull & Automated Remediation
-
When an email later identified as malicious is detected, the system automatically pulls it from all users' inboxes.
-
Reduces response time from hours to minutes.
-
-
Advanced Authentication Controls
-
Supports authentication and email encryption to prevent sensitive data from being sent outside the organization.
-
-
-
User Awareness & Human Risk Management Strengthening the organization's human firewall — because "people" are the last line of defense against all attacks.
Key Capabilities:
-
Phishing Simulation to test user awareness.
-
Interactive Awareness Training programs on security.
-
User Risk Scoring to assess and rank individual user risks.
-
Analyzes click-through behavior on links or attachments to help security teams tailor training strategies effectively.
-
-
Information Protection & Data Loss Prevention (DLP) A solution to prevent sensitive data leakage, both internal and external.
Key Features:
-
Detects sensitive information such as customer data, national ID numbers, or financial data attempting to be sent via email or cloud.
-
Analyzes content and context to differentiate anomalous behavior from normal usage.
-
Auto Encryption of sensitive data and Access Control for files.
-
-
Cloud & Collaboration Security Protecting collaboration on cloud platforms such as Microsoft 365, Google Workspace, and internal communication tools.
Key Features:
-
Detects excessive file sharing or unauthorized data dissemination.
-
Prevents connections from potentially malicious external OAuth Apps.
-
Provides comprehensive visibility and control over user activities in SaaS (CASB Functionality).
-
-
Threat Intelligence & Digital Risk Protection An external threat monitoring system that helps organizations see "what's happening outside their network boundaries."
Key Features:
-
Dark Web Monitoring & Data Leak Detection
-
Detects leaked organizational data, such as credentials, tokens, database dumps, or employee information, that is posted or traded on the Dark Web — before it can be exploited by malicious actors.
-
-
Early Warning & Preemptive Defense
-
When the system detects a leak, it immediately sends an alert, allowing security teams to reset accounts, close APIs, or restrict access before an attack occurs.
-
-
Brand & Domain Impersonation Monitoring
-
Monitors for the creation of fake websites or domains impersonating the organization for phishing campaigns or user deception.
-
-
Threat Actor Tracking & Intelligence Correlation
-
Analyzes the behavior of threat actors and correlates this information with internal system events to identify the source of threats and future attack trends.
-
-
-
Integrated Cyber Defense Platform The integration between "email protection" and "external threat monitoring" systems provides organizations with a comprehensive security view encompassing Prevention – Detection – Response.
Examples of Collaboration:
-
If a fake domain is found being used on the Dark Web → The email system automatically updates its policy to block that domain.
-
When a phishing email is received → The Threat Intelligence system can investigate and correlate it with activities on the dark web to find the source of the threat.
-
If user data is found being sold on the dark market → The DLP system immediately enforces encryption policies and password resets.
The result is the creation of a "cyber security lifecycle" that is automatically responsive, proactive in prevention, and reduces both internal and external risks.
-
Overview This solution is designed based on a Human & Intelligence-Centric Security concept, integrating technology that protects "users – data – emails – and external information." This ensures that every layer of defense communicates intelligently, not only detecting and blocking threats but also seeing deep into the root causes of risks before an attack occurs.









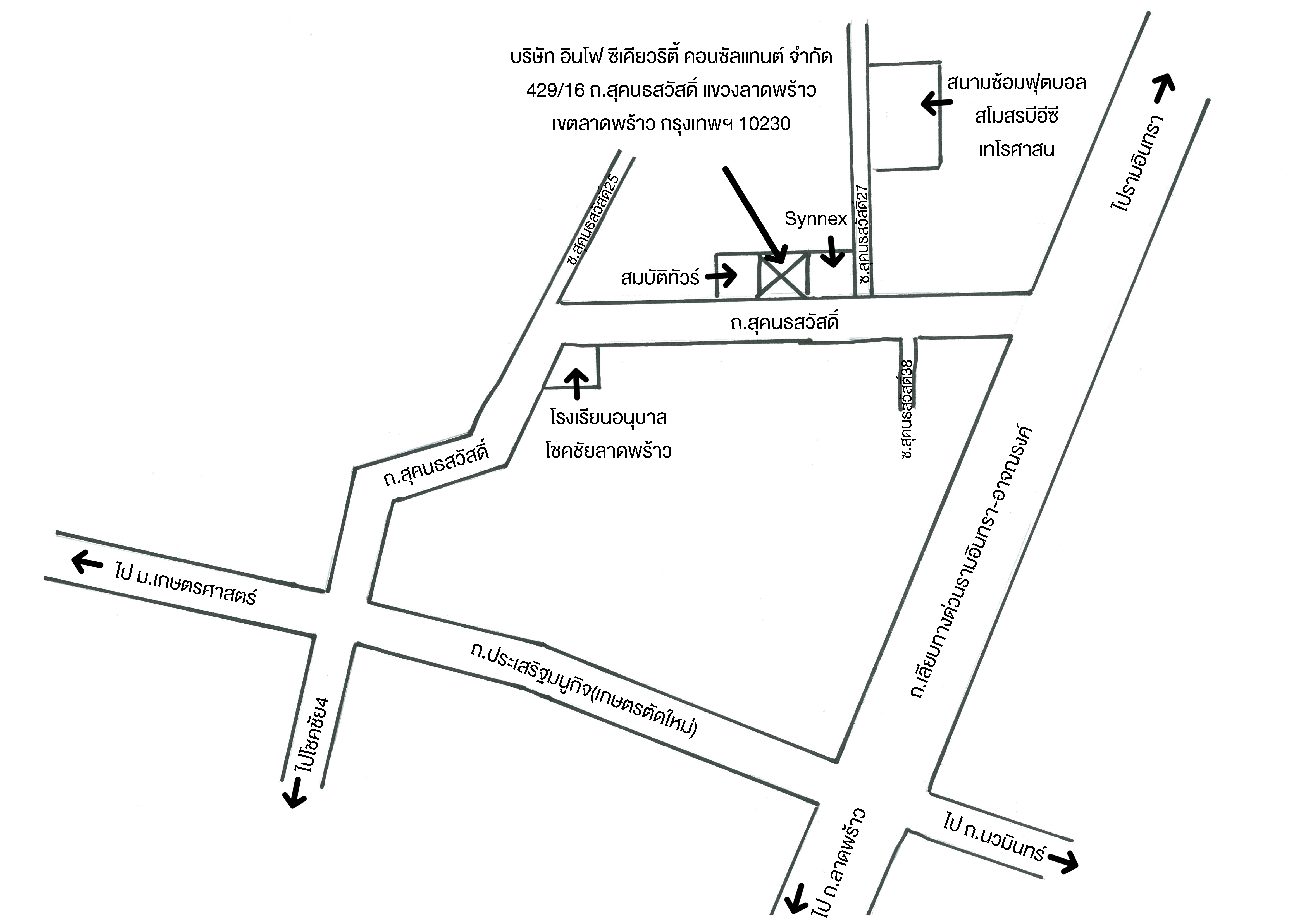
 GOOGLE MAP
GOOGLE MAP INFOSEC MAP
INFOSEC MAP